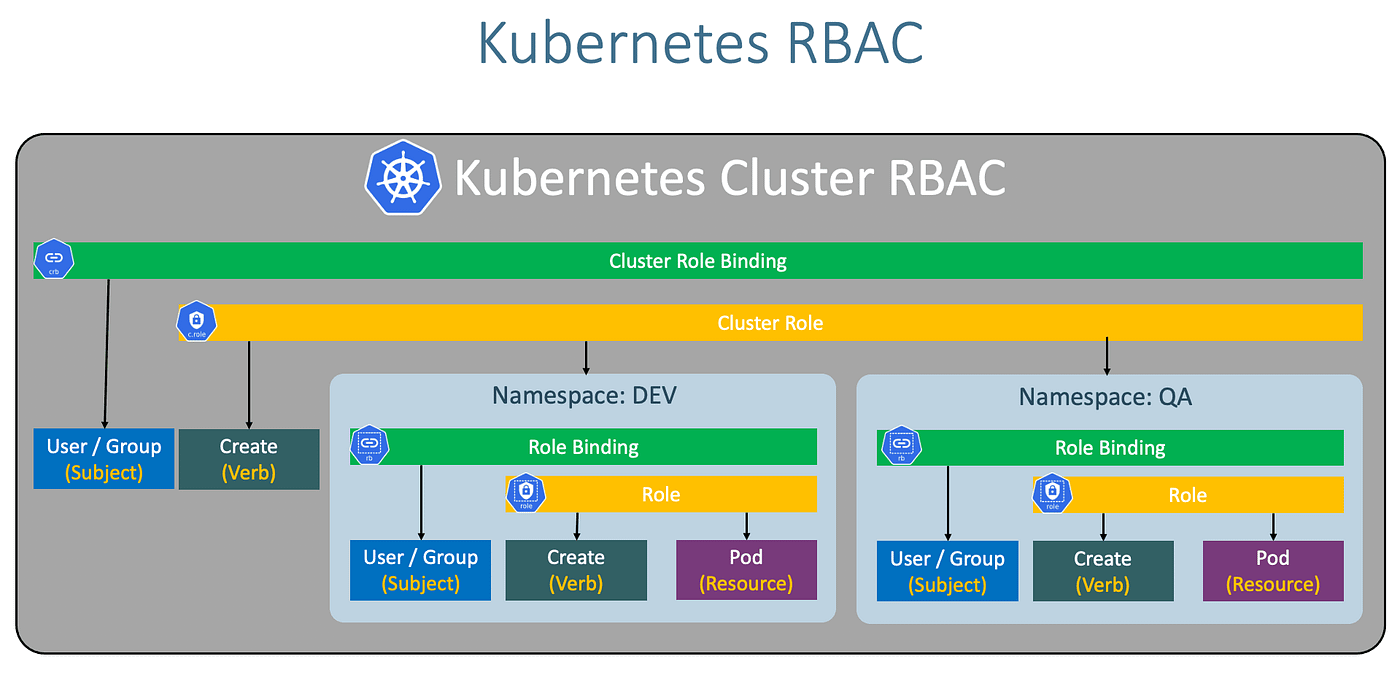
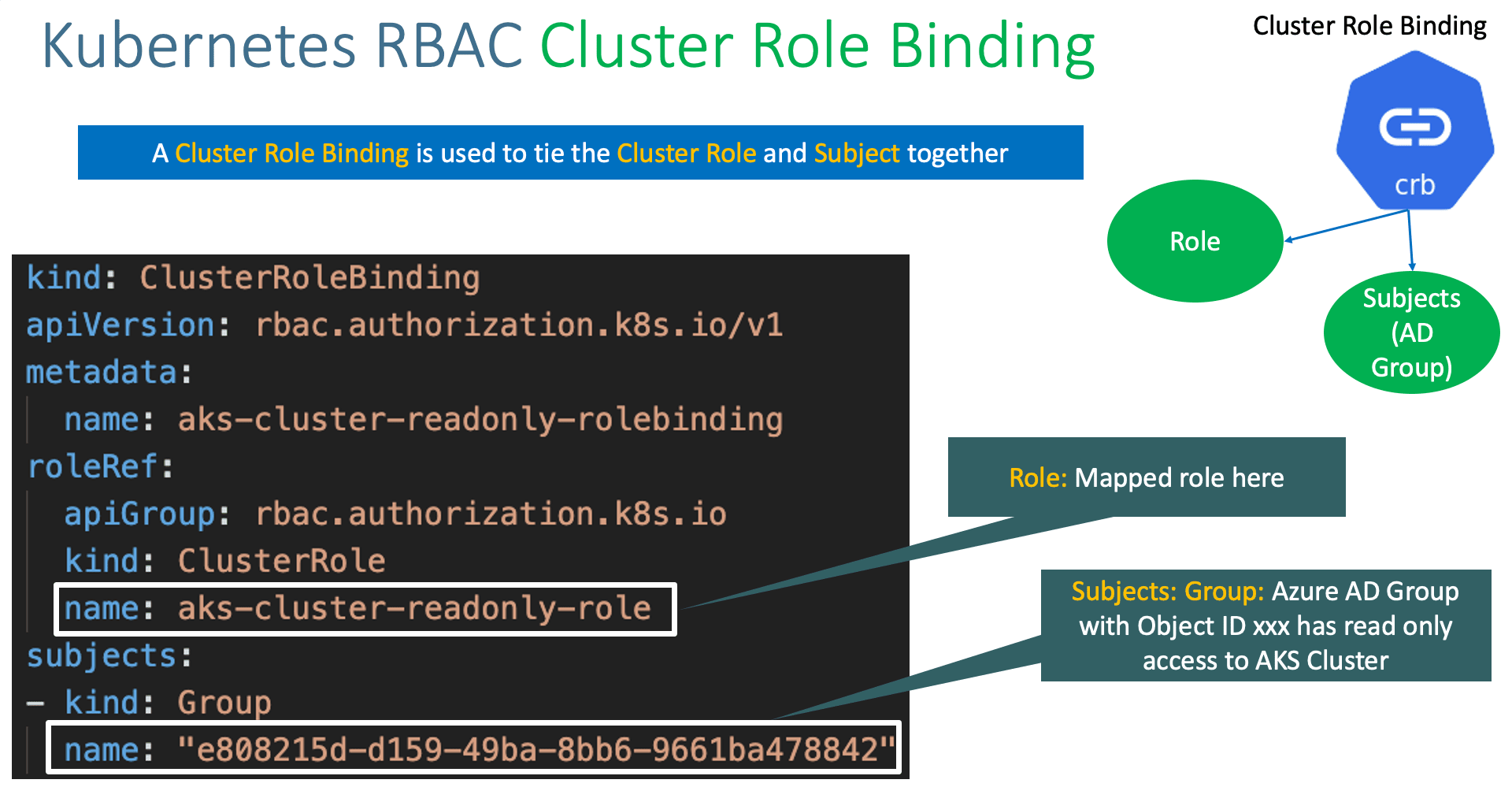
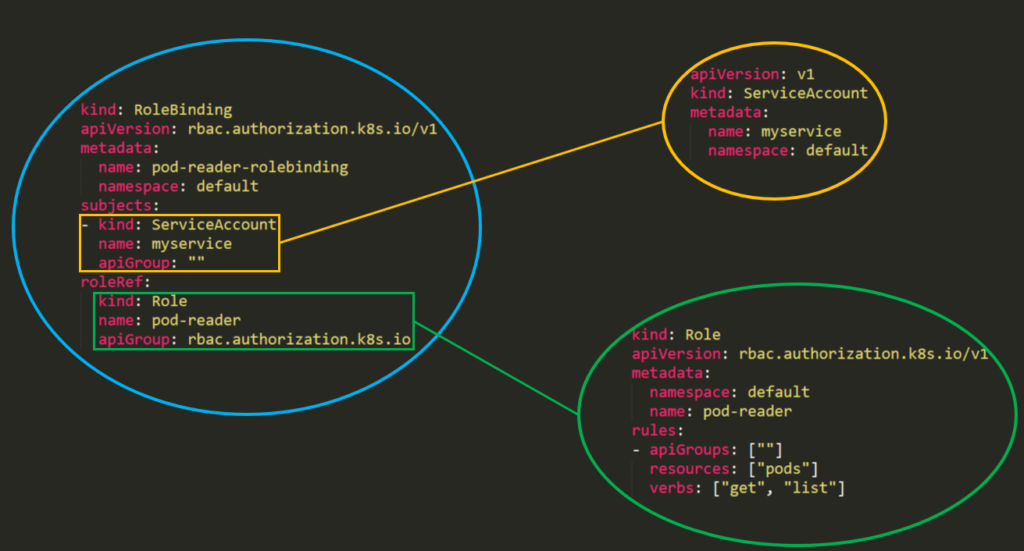
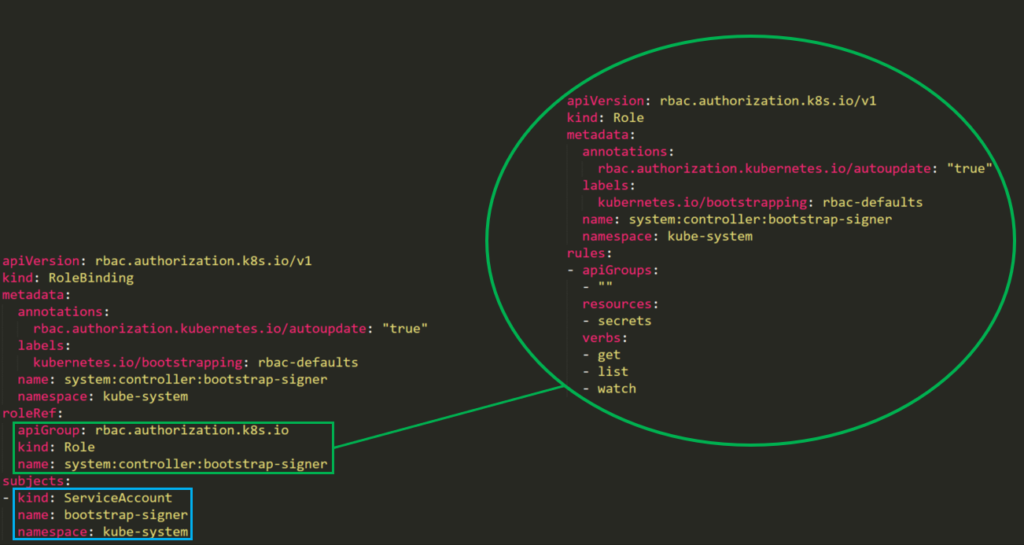
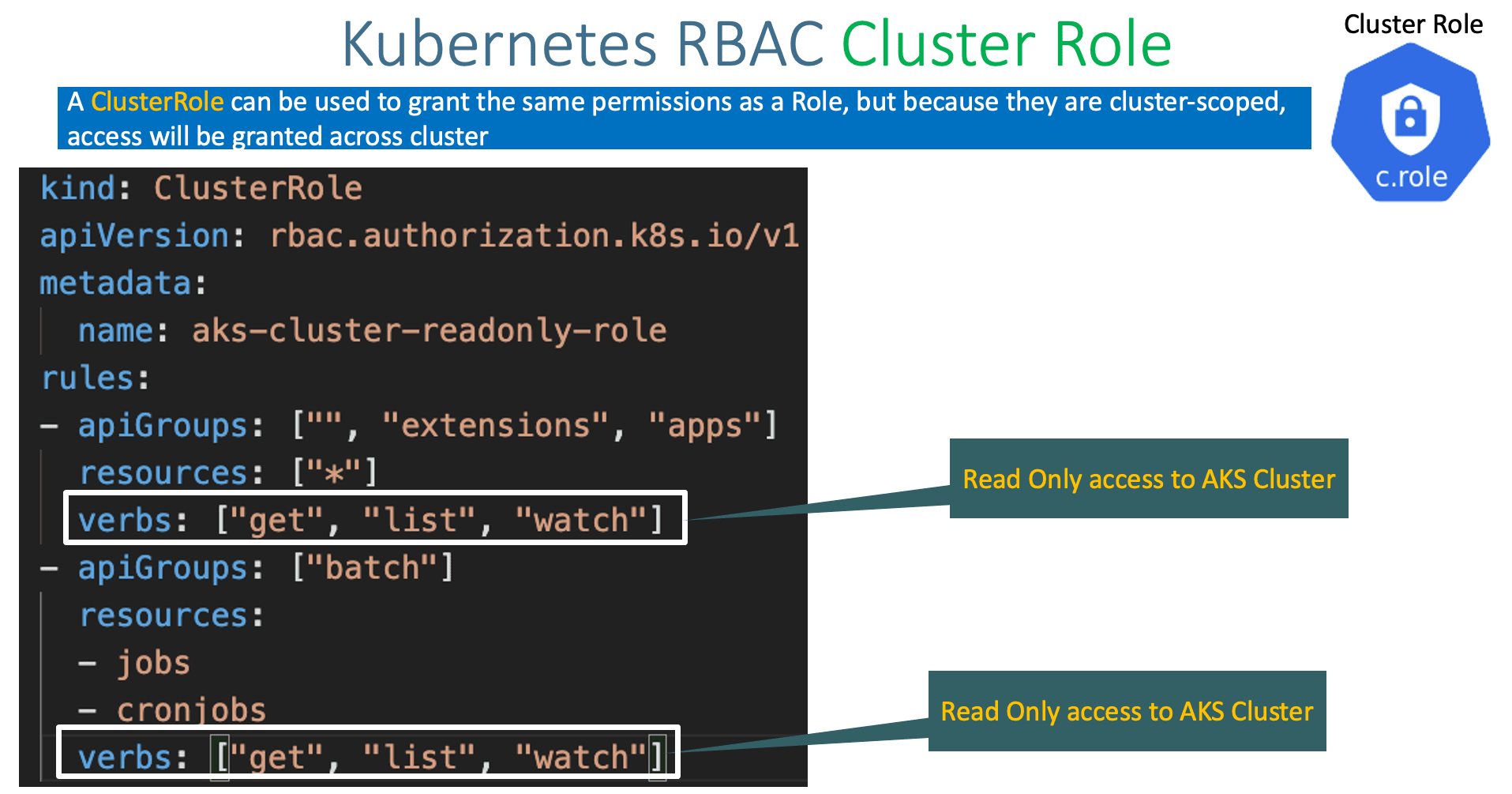
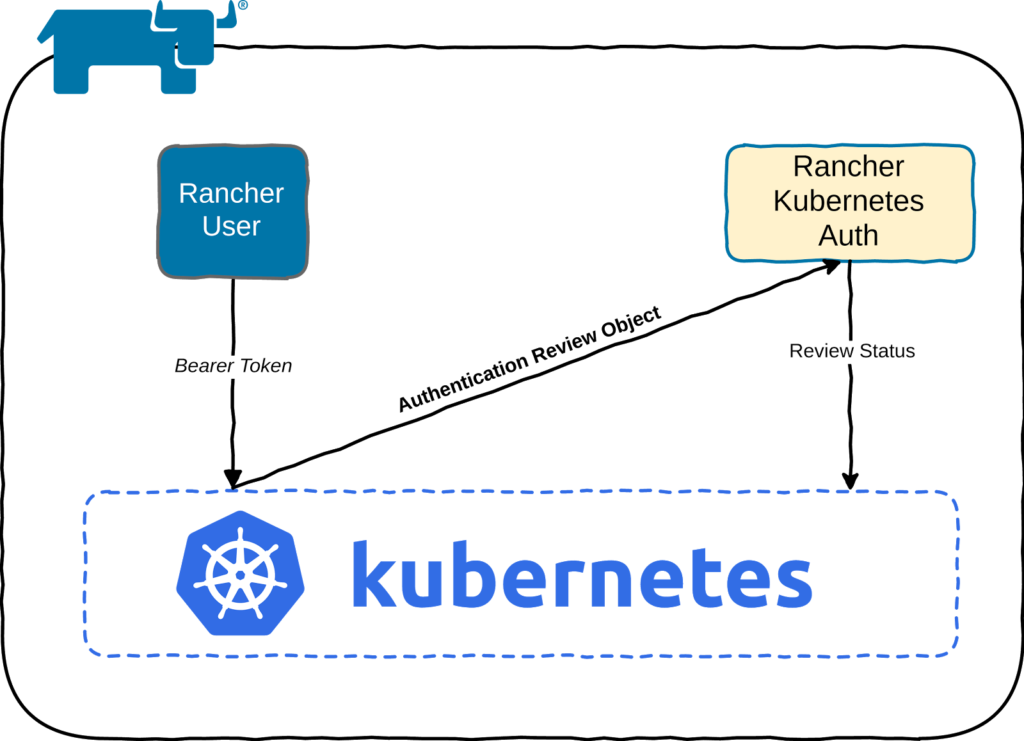
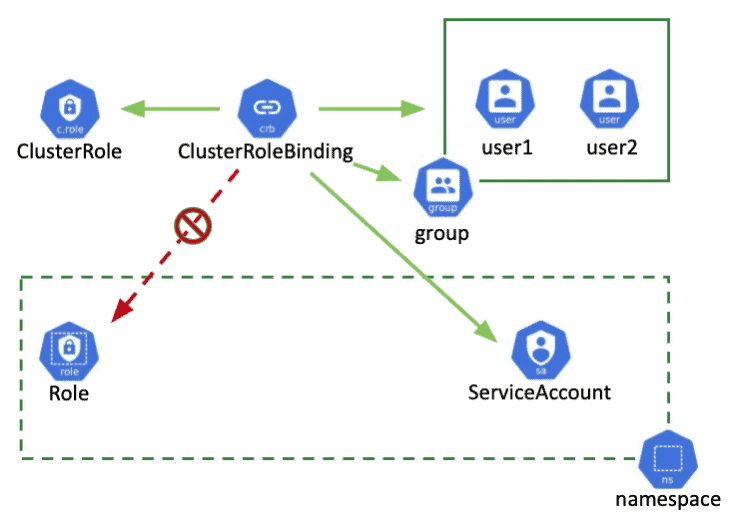
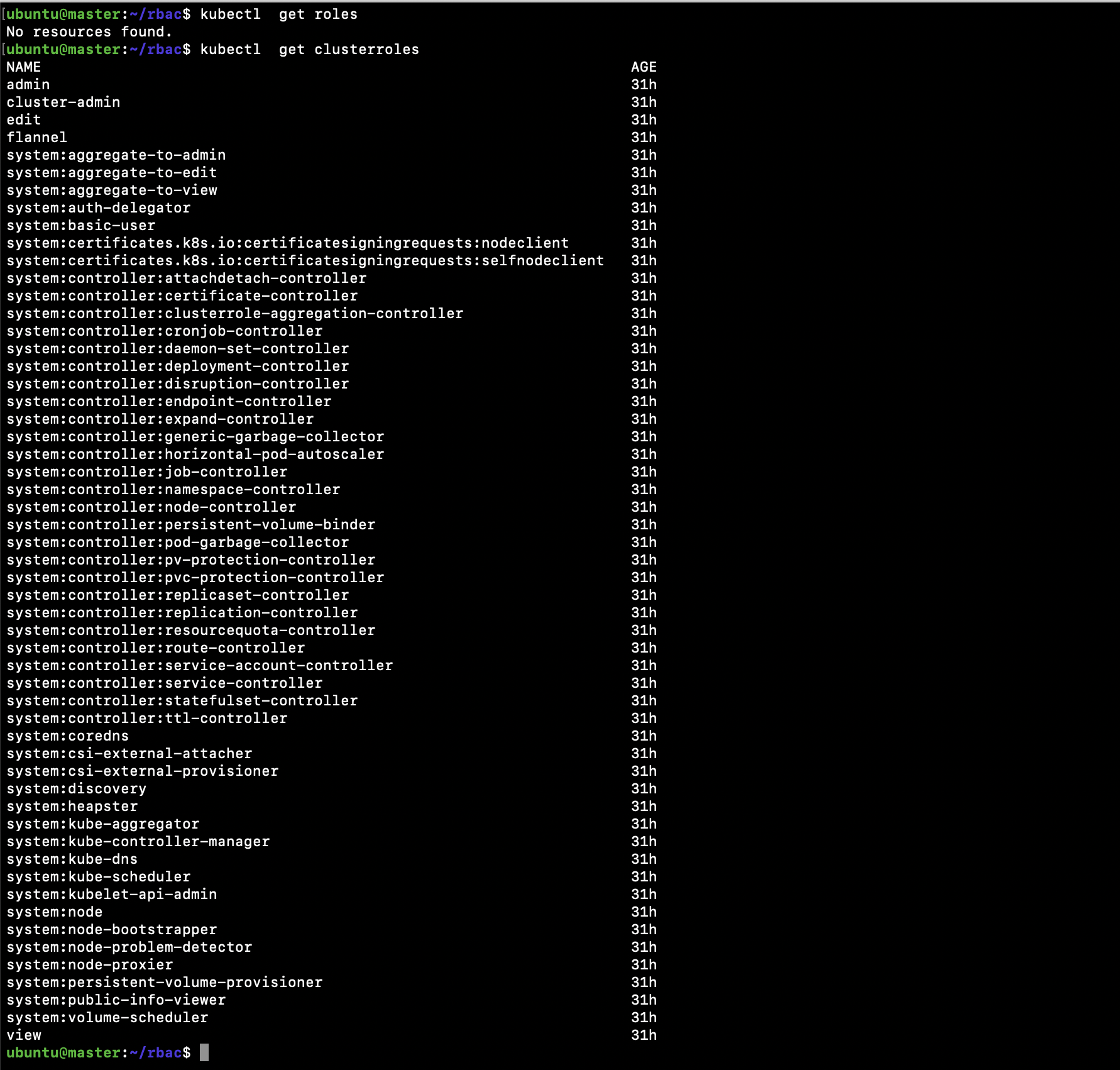
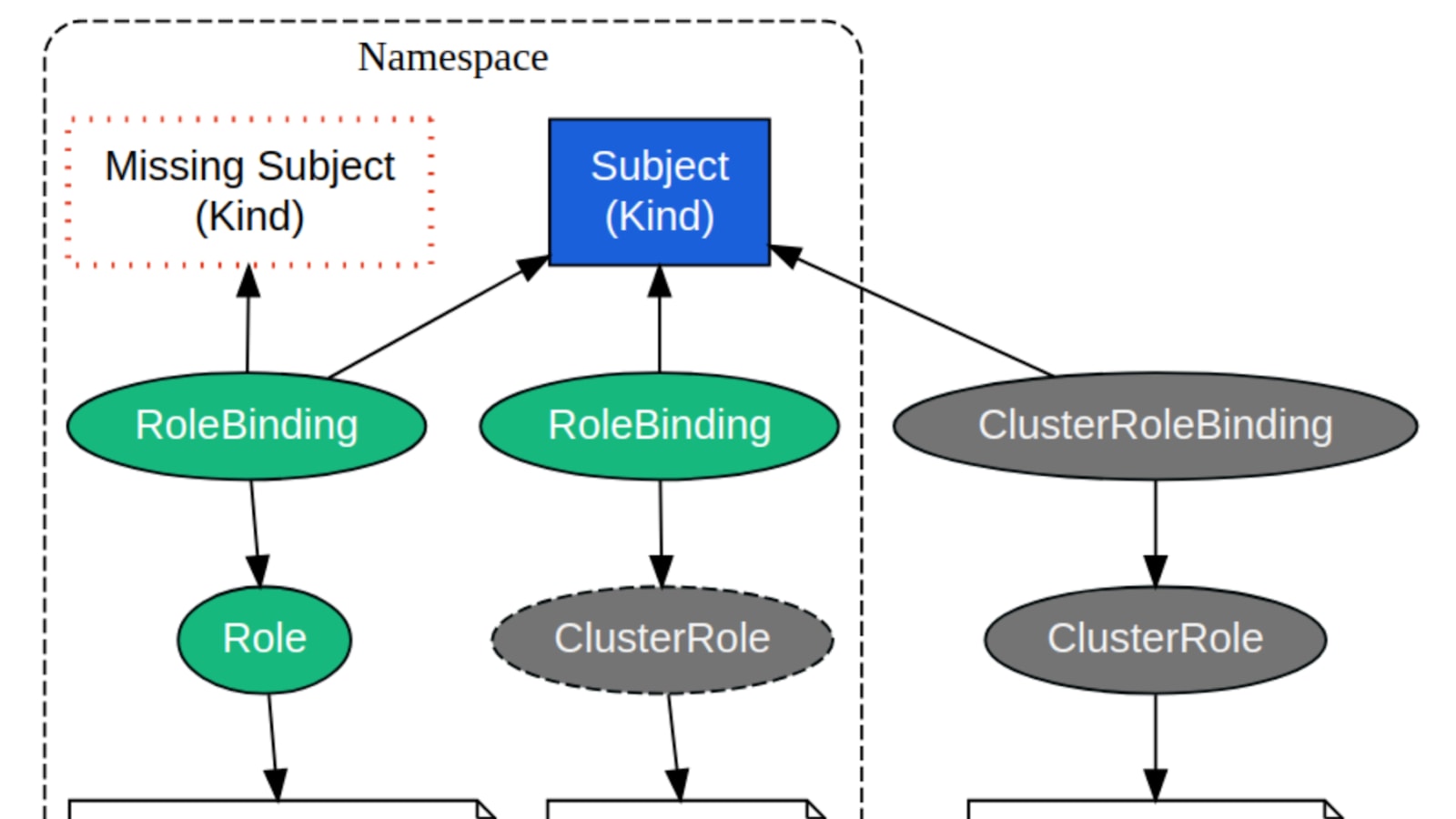
Give Users and Groups Access to Kubernetes Cluster Using RBAC | by Md Shamim | FAUN — Developer Community 🐾
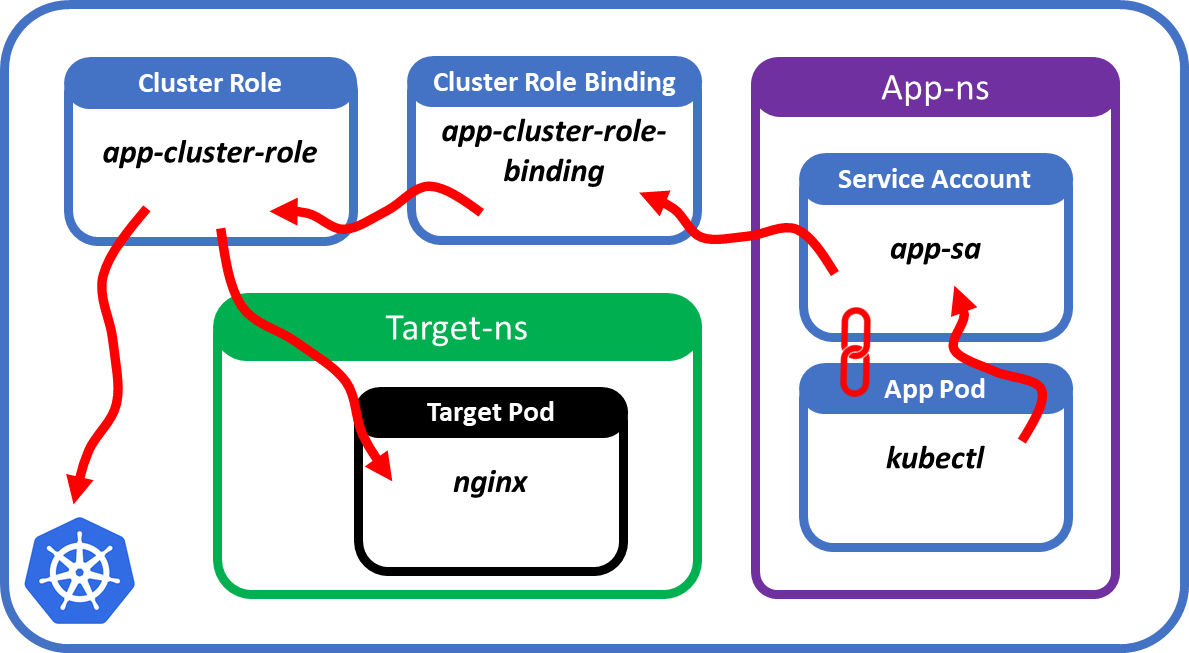
Unleashing the Power of Kubernetes: Deploying Containers with Cluster Resource Access for KCP-Edge | by Franco Stellari | Feb, 2023 | ITNEXT | ITNEXT
Any Idea why the `can-i` command is saying no even I have proper permission set . . . - Kubernetes - KodeKloud - DevOps Learning Community

The Bind, Escalate and Impersonate Verbs For Privilege Escalation In The Kubernetes Cluster | by Yani | InfoSec Write-ups

kubernetes - How to view the permissions/roles associated with a specific service account in k8s? - Stack Overflow

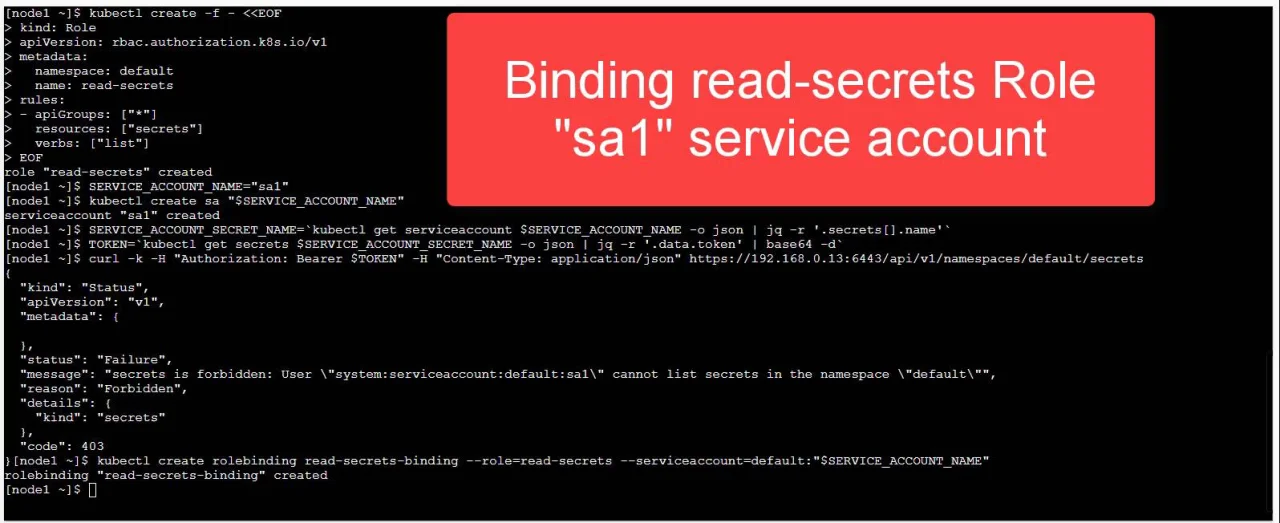
RBAC with Kubernetes in Minikube. This tutorial will guide you on how to… | by Houssem Dellai | Medium